[ad_1]
On Monday, the cross-chain token bridge Nomad was attacked and hackers managed to siphon $190 million from the protocol, draining a fantastic majority of the funds. The Nomad cross-chain bridge assault was the third-biggest crypto heist of 2022, and the ninth largest of all time.
Nomad Cross-Chain Bridge Exploited for $190 Million
Cross-chain bridges on this planet of decentralized finance (defi) simply can’t catch a break irrespective of how lengthy they’ve been working and even after the bridges have been audited. On August 1, 2022, the cross-chain bridge Nomad suffered an assault that noticed the bridge lose $190 million in crypto funds. Safety consultants on the blockchain auditing agency Certik revealed an incident report describing what occurred.
“The vulnerability was within the initialization course of the place the “committedRoot” is ready as ZERO,” Certik wrote. “Subsequently, the attackers have been capable of bypass the message verification course of and drain the tokens from the bridge contract,” Certik added, noting:
The exploit occurred when a routine improve allowed verification messages to be bypassed on Nomad. Attackers abused this to repeat/paste transactions and have been capable of drain the bridge of almost all funds earlier than it may very well be stopped.
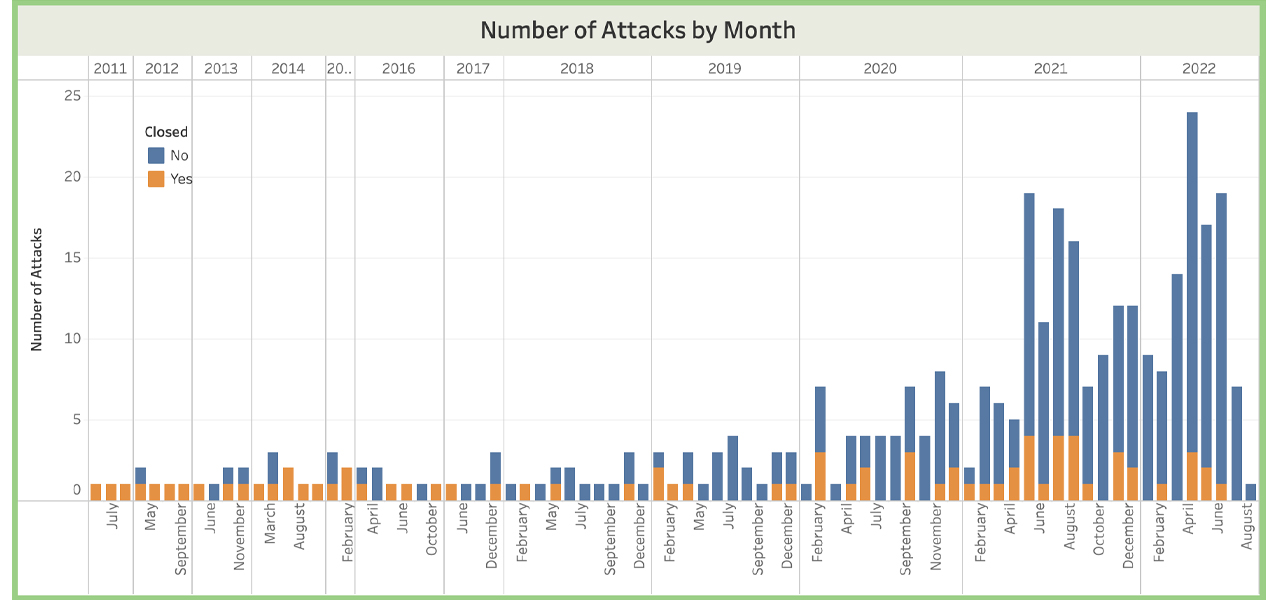
Cross-chain bridges have been affected by exploit after exploit since they have been first launched. On the finish of March, the biggest hack of 2022 noticed $620 million stolen from Axie Infinity’s Ronin bridge. Researchers at Comparitech element that the Nomad bridge assault was the third-largest breach this yr, in line with the analysis agency’s crypto heist tracker. Whereas Nomad related quite a lot of blockchain networks, the founder and CEO of AVA Labs, Emin Gün Sirer, tweeted concerning the incident and mentioned the AVAX bridge was secure.
“The Nomad bridge, utilized by non-Avalanche chains, was hacked at present,” Gün Sirer wrote. “Nomad was the official bridge for EVMOS (Cosmos EVM), Moonbeam (Polkadot EVM), and Milkomeda (one other EVM) — The Avalanche Bridge is unaffected.”
Nomad Raised $22 Million in April, Blockchain Safety Firm Certik Says This Explicit Bug ‘Would Be Troublesome to Uncover Underneath Standard Auditing Practices’
The assault in opposition to the Nomad bridge follows the challenge elevating roughly $22.4 million in seed funding in a finance spherical led by Polychain Capital. Different strategic traders that helped Nomad increase funds embody 1kx, Ethereal Ventures, Hack.vc, Circle Ventures, Amber, Robotic Ventures, Hypersphere, Figment, Dialectic, Archetype, and Ledgerprime. Whereas a broad audit might have discovered the Nomad bridge vulnerability, the blockchain and good contract auditors from Certik say this assault could also be harder to search out in a traditional audit.
“One of these situation can be tough to find beneath typical auditing practices that assume all deployment configurations are appropriate, as a result of this explicit bug was launched by errors within the deployment parameters,” Certik’s report on the Nomad state of affairs concludes. “Nonetheless, a broader auditing course of and full-scope penetration take a look at that features validating deployment processes would probably seize this bug,” the auditors added.
What do you consider the current cross-chain exploit in opposition to the Nomad bridge? Tell us what you consider this topic within the feedback part under.
Picture Credit: Shutterstock, Pixabay, Wiki Commons, Comparitech,
Disclaimer: This text is for informational functions solely. It isn’t a direct provide or solicitation of a suggestion to purchase or promote, or a advice or endorsement of any merchandise, providers, or corporations. Bitcoin.com doesn’t present funding, tax, authorized, or accounting recommendation. Neither the corporate nor the writer is accountable, immediately or not directly, for any harm or loss brought on or alleged to be attributable to or in reference to using or reliance on any content material, items or providers talked about on this article.
[ad_2]
Source link


























