[ad_1]
In context: Regardless that victims have began to refuse to pay cyber-criminals to get their unencrypted information again, the ransomware enterprise remains to be probably the most harmful threats to firms and authorities organizations. Native establishments could be a significantly “scrumptious” meal for ransomware operations, as disrupting their IT providers means making on a regular basis folks’s life a lot tougher.
The town of Dallas was not too long ago hit by a ransomware assault, which compelled native directors to briefly cease providing some IT providers whereas officers scramble to isolate the an infection and take away the malware from already contaminated techniques. Dallas is the fourth-largest metropolitan space within the U.S. with 7.5 million residents, so the ransomware an infection will doubtless present many complications to lots of people.
In accordance with native experiences later confirmed by different sources and safety professionals, Dallas IT providers had been contaminated by the Royal ransomware. Ransom notes started coming out of community printers yesterday, mocking the victims with a “distinctive deal” and a suggestion to offer extra safety whereas threatening to publish confidential recordsdata on-line if the “modest royalty” is just not paid by a Darkish Website.
Royal is an alleged spinoff of the Conti ransomware, because the malicious operation began its actions in the beginning of 2022 after Conti was shut down by its operators. On the finish of 2022, Royal was probably the most energetic ransomware-based threats in opposition to enterprise and authorities organizations.
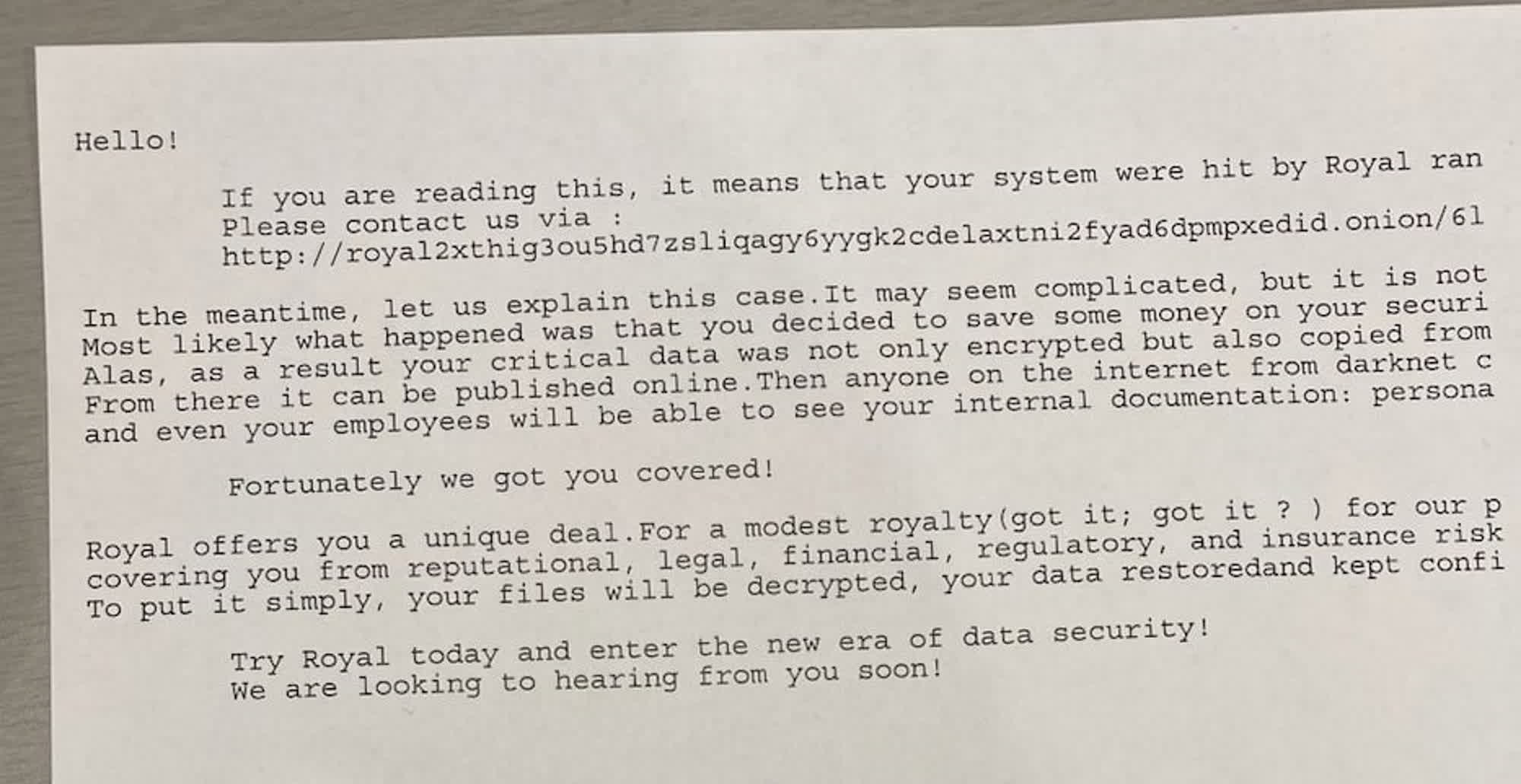
The Royal an infection impacted a few of the vital IT providers offered by the Dallas administration, together with the 911 dispatch system and the Dallas County Police Division web site. Moreover, Dallas’ courtroom system was compelled to cancel all deliberate jury trials and jury responsibility beginning Might 2nd.
The Metropolis of Dallas has confirmed the assault, saying that the Metropolis’s safety monitoring instruments notified the native Safety Operations Middle (SOC) a couple of potential ransomware an infection. The Metropolis later confirmed that the malware compromised “numerous servers” impacting a few of its providers. The “Metropolis staff” and its safety distributors are actually busy isolating the ransomware to stop its spreading, whereas eradicating the malware from already contaminated techniques. The impression for Dallas residents ought to be “restricted” anyway, native authorities mentioned.
Royal’s modus operandi relies on focused callback phishing assaults, the place cyber-criminals impersonate meals supply or software program suppliers in e-mail messages pretending to be subscription renewals. The messages ask the potential victims to name the included telephone numbers, attempting to persuade folks to put in distant entry software program to compromise the company community.
[ad_2]
Source link





/cdn.vox-cdn.com/uploads/chorus_asset/file/25524175/DSCF8101.jpg)





















